Quoted Items
Internet Fraud Alert
It has come to our attention that malicious phishing emails fraudulently pretending to originate from Parker Steel Company are being sent out. We take information security very seriously to prevent fraud and protect the interests of Parker Steel Company and our customers/vendors.
Keep these simple rules in mind to better protect yourself against email fraud:
- Never send sensitive personal or financial information through email.
- Don’t open email attachments unless you trust the source.
- Don’t follow links in an email asking for sensitive personal or account information, even if the source looks familiar.
- Consult with you Information Technology department or resource about any phishing attempts.
- Ask questions. If you’re suspicious of a message, call us to validate communications originating from Parker Steel Company.
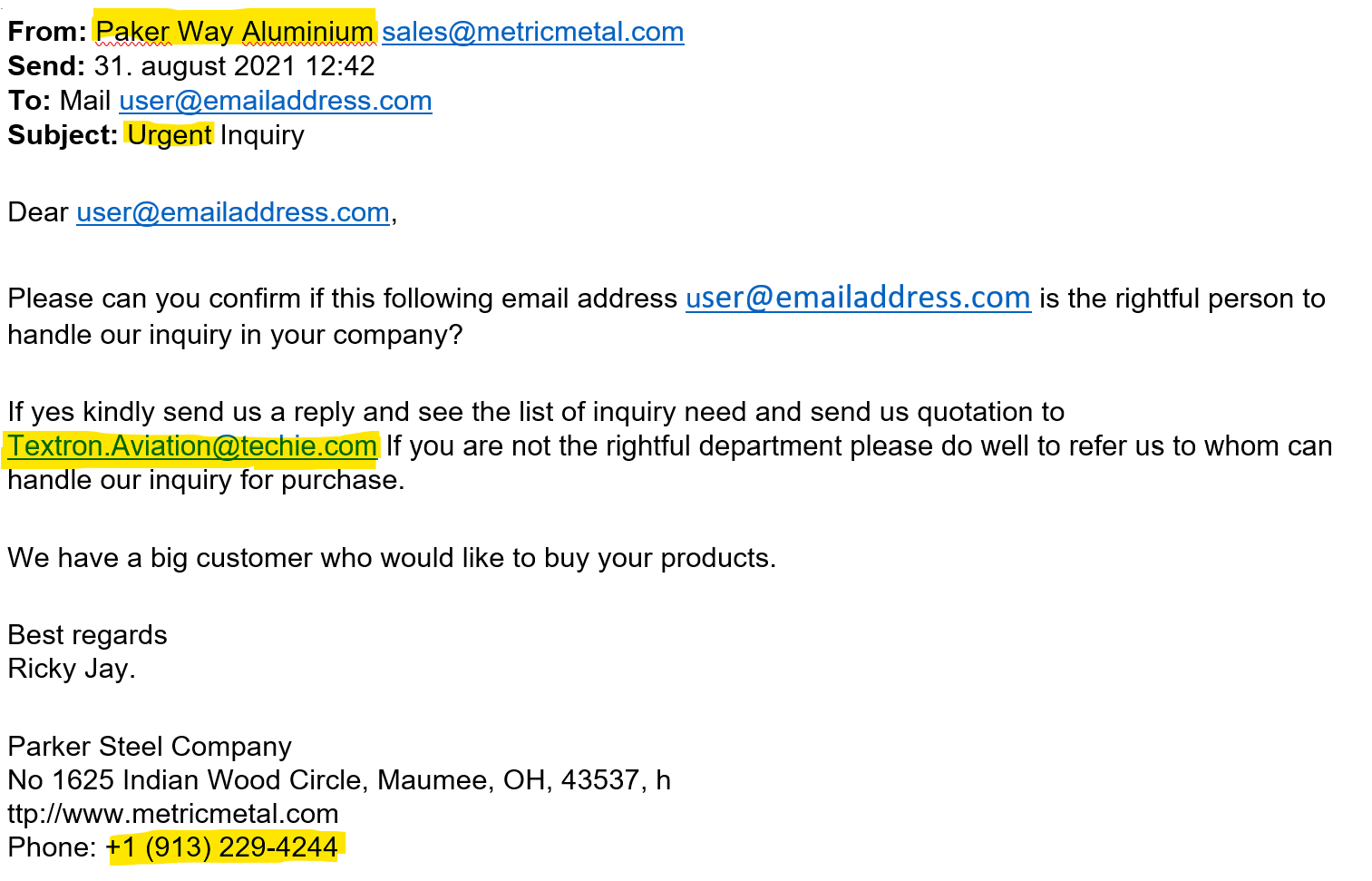
Here is an example of a fraudulent email request with some of the red flags highlighted…
- Note the misspelling & change of the Parker Steel Company name in the From section
- Many of these fraudulent emails with push urgency in order to have the recipient/s overlook some details.
- The request to reply with information to a different email address not associated with Parker Steel’s email domain @metricmetal.com.
- The name of a person and a phone number not associated with Parker Steel Company.
Information on Spoofing and Phishing from: https://www.fbi.gov/scams-and-safety/common-scams-and-crimes/spoofing-and-phishing
Spoofing is when someone disguises an email address, sender name, phone number, or website URL—often just by changing one letter, symbol, or number—to convince you that you are interacting with a trusted source.
For example, you might receive an email that looks like it’s from your boss, a company you’ve done business with, or even from someone in your family—but it actually isn’t.
Criminals count on being able to manipulate you into believing that these spoofed communications are real, which can lead you to download malicious software, send money, or disclose personal, financial, or other sensitive information.
Phishing schemes often use spoofing techniques to lure you in and get you to take the bait. These scams are designed to trick you into giving information to criminals that they shouldn’t have access to.
In a phishing scam, you might receive an email that appears to be from a legitimate business and is asking you to update or verify your personal information by replying to the email or visiting a website. The web address might look similar to one you’ve used before. The email may be convincing enough to get you to take the action requested.
But once you click on that link, you’re sent to a spoofed website that might look nearly identical to the real thing—like your bank or credit card site—and asked to enter sensitive information like passwords, credit card numbers, banking PINs, etc. These fake websites are used solely to steal your information.
Phishing has evolved and now has several variations that use similar techniques:
- Vishing scams happen over the phone, voice email, or VoIP (voice over Internet Protocol) calls.
- Smishing scams happen through SMS (text) messages.
- Pharming scams happen when malicious code is installed on your computer to redirect you to fake websites.
Spoofing and phishing are key parts of business email compromise scams.
If you have any questions or concerns, please contact Parker Steel Company and thank you for your vigilance.
